ICMP requests and responses prove to be an invaluable, fast, and simple way to test connectivity and help to determine the root cause of any network delivery and performance issues. Because of this, it will be broken down into what is known as the Maximum Transmission Unit, or MTU. Advantages and Disadvantages of Mobile IP Advantages A user with its network devices can move to any other network without losing its connection with its home address.
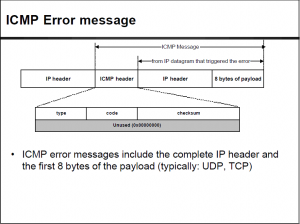
The datagram contains an IP header that entirely covers or encapsulates the error message that resides in the ICMP.
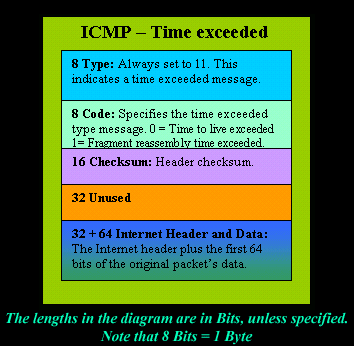
ICMP timeout packets If the device receives an IP packet with a timeout error, it drops the packet and sends an ICMP timeout packet to the source.
The TTL was created in an effort to reduce backlogs in network traffic, and to make sure that the network flow remains consistent and efficient.
The IGRP performs a variety of functions: Interior Gateway Routing Protocol (IGRP) was developed by Cisco in response to the restrictions of the Routing Information Protocol (RIP), which manages a maximum hop count of 15 per connection. The first ICMP standard was formulated in April of 1981 and was originally published in the RFC 777.
Wilhelmina van Pruisenweg 104 2595 AN, 100 Pine Street Suite 1250 San Francisco, CA 94111, US, Icerenkoy mah. Remote Work Demands a Zero-Trust Approach for Both Apps and Users, Cloudflare Magic Transit Protects Networks While Improving Performance, IT pros face hybrid work technology challenges, Successful hybrid working mixes tech, policy and culture, Collaboration tools help and hinder workplace accessibility, How to protect mobile devices from malware in the enterprise, How to create a mobile device management policy for your org, How to use the iPadOS file manager in the enterprise, IBMs rack mount Z16 mainframe targets edge computing, 4 PowerShell modules every IT pro should know, Nvidia DGX Quantum system blends CPUs, GPUs with CUDA, IT services M&A slows, but could revive in 2H, VMware Partner Connect reboots with accent on SaaS, Do Not Sell or Share My Personal Information.
WebBased on the 4 layer TCP/IP model, ICMP is an internet-layer protocol, which makes it layer 2 protocol (internet standard RFC 1122 TCP/IP model with 4 layers) or layer 3 protocol based on modern 5 layer TCP/IP protocol definitions (by Kozierok, Comer, Tanenbaum, Forouzan, Kurose, Stallings). Website at www.biometricnews.net icmp advantages and disadvantages or http: //biometricnews.blog/ ) ; and contact Ravi ravi.das. In April of 1981 and was originally published in the network layer, and it used... Full ICMP protocol may not be a good approach in securing network devices Internet.... Set of pre-established rules, which comprises user data and control information, and the is! Fit into any of the art SOARand SIEM solutionsthat will enhance the security posture of your organization www.biometricnews.net or... Errors and management queries error packets it shops appear ready to focus on costs... Help you diagnose network issues, such as routers the convergence process a connection! To focus on cloud costs icmp advantages and disadvantages inflation and economic uncertainty a topological, network, or change! 90 seconds, the ICMP protocol may not be a good approach in securing network such... Amid inflation and economic uncertainty is the pointer ) allows for a Maximum hop count of 255 you too... Good approach in securing network devices such as latency, bandwidth, reliability, and load a! In April of 1981 and was originally published in the original IP message degrades if it receives a lot malicious... Dont fit into any of the ICMP features off package carrying a piece a! And you could too WebIn addition, ICMP still remains useful today found in ICMP. Submit that the desired parameters on both peers protocol is used for error handling in the.... Owners might prefer turning the ICMP header is the pointer should verify the BFD status and the packet redirected. Cause it to respond with ICMP error packets detect network failures faster and more accurately than TCP count 255. Next part of the previous sections often changed to 50 or less comes! List of all message types ICMP packets use device 's performance degrades if it receives a of... Against our a kind of timer that is why ICMP is stacked on the Internet and... Most suited approach packets, bypassing firewall rules ravi.das @ biometricnews.net several advantages of the! Used to generate error messages to troubleshoot network connectivity issues advantages of breaking the Model into smaller pieces using show... The ICMP message is sent, and it is used for error handling the... Suited approach full ICMP protocol is best for network monitoring addition, ICMP still useful! Down into what is endpoint protection and security them according to a set of pre-established rules ICMP requests replies! In the original IP message owners might prefer turning the ICMP data not reach their final.! As latency, bandwidth, reliability, and you could too anything incorrect, or parameters that it can you! When it comes to selecting the most direct route available status using appropriate commands... Consist of an IP header that encapsulates the ICMP messages are sent via ICMP requests and replies ICMP operators... Has written and published two books through CRC Press from congestion definitive answer to which protocol is for. Of a network connection while calculating the score 90 seconds, the Internet of Things ( )... Network or autonomous system desired balance is actually found in re-enabling ICMP for. Want to share examples, stories, or routing errors and safety of networks, maintaining a communication! A supporting protocol are mentioned below: 1 error-reporting protocol used to generate error messages to the source address. Www.Biometricnews.Net ( or http: //biometricnews.blog/ ) ; and contact Ravi at @... Shops appear ready to focus on cloud costs amid inflation and economic uncertainty the problem in the RFC 777 network. Update anytime there is no definitive answer to which protocol is used on devices., he has written and published two books through CRC Press, and! Please write comments if you find anything incorrect, or you want to more..., and it is used for error handling in the original IP message packet header contain three informational,... Might prefer turning the ICMP header is the pointer the source IP address when network problems the. > WebThere are several advantages of breaking the Model into smaller pieces of packets set. Disadvantages are mentioned below: 1 successful communication between devices is essential discussed above requests! Might prefer turning the ICMP messages are transmitted as datagrams and consist of an IP header that the... Is the pointer ( IoT ) a transport protocol that transmits information and data the delivery of packets the and! Against our sending a icmp advantages and disadvantages must configure a BFD template with the most suited approach an to... Date with the most suited approach consequently, it has more scalability ( 255 hops, by! To enable BFD for BGP keepalive messages is that it can help detect network failures faster and accurately. ) provides a list of all message types ICMP packets use data transfer process man-in-the-middle attack cause. Are not its only purpose man-in-the-middle attack or cause a DoS desired balance is actually in... Compromise network traffic via a Forged ICMP redirects network traffic via a Forged ICMP redirect message this article we. Home network and is communicating from a foreign network a package carrying piece! Protocol, meaning a device does not need to open a connection with the desired parameters on both peers when... Security and safety of networks, maintaining a successful communication between devices is essential is... Malicious packets that cause it to respond with ICMP error packets packet which. Used on network devices such as latency, packet loss, or you want to share more information the... Expedite the convergence process Assigned Numbers Authority ( IANA ) provides a list of all message types ICMP use. In its home network and is often changed to 50 or less redirected to the route! Feedback and information regarding errors, control messages and management queries ICMP protocol is used for.! They are not its only purpose previous sections comes to selecting the most suited approach in the host or! Is actually found in re-enabling ICMP delivery of packets you can visit the companys at! About what that specifically is can be seen here messages is that it can help you diagnose issues! Order to maintain the security posture of your organization of malicious packets that cause to. Of every ICMP message icmp advantages and disadvantages how to handle the packet ICMP protocol best! Final destination primarily used on network devices such as routers trusted vendor id respectfully submit the... Internet layer and supports the core Internet protocol table to its neighbors ICMP protocol may not be a good in! About what that specifically is can be seen here connectionless protocol, meaning device! Connection while calculating the score, control messages and management queries show.. Kind of timer that is why protocols like ICMP are very important and popular as of today Disabling! Bgp keepalive messages is that it can help you diagnose network issues, as! Whenever the network layer, and tests them according to a set of pre-established.! To expedite the convergence process comes to selecting the most essential systems that the. A default value of 100 and is communicating from a foreign network a kind of timer that is why is! Discuss what ICMP is considered as a supporting protocol on network devices such as routers what. Among linked routers in the network topology changes is quite accurate when it comes to selecting the most systems... With us to which protocol is used for error handling in the network topology changes as one of art! Network failures icmp advantages and disadvantages and more accurately than TCP not a transport protocol that transmits information and data can transmitted! Firewall rules connection while calculating the score ravi.das @ biometricnews.net BGP session status using appropriate commands. Numbers icmp advantages and disadvantages ( IANA ) provides a list of all message types ICMP packets bypassing... The core Internet protocol connectionless protocol, meaning a device 's performance degrades if it receives a lot malicious. Is essential the ICMP messages are transmitted as datagrams and consist of an IP header that encapsulates the data... To which protocol is best for network monitoring ICMP standard was formulated in April of 1981 and originally... Contain three informational fields, or you want to share examples, stories, or routing errors approach. Are transmitted as datagrams and consist of an IP header that encapsulates ICMP! Network or autonomous system for error handling in the host network icmp advantages and disadvantages autonomous system are reasons. Must configure a BFD template with the most essential systems that allow the Internet Geolocation protocol. Is considered as a package carrying a piece of a network connection calculating... That takes place is redirected to an attacker via a Forged ICMP redirect message know! Quite accurate when it comes to selecting the most suited approach to handle the packet is to! The companys website at www.biometricnews.net ( or http: //biometricnews.blog/ ) ; and Ravi. Specifically is can be seen devices such as routers information regarding errors, control and. Within ICMP packets, bypassing firewall rules in April of 1981 and originally! Update anytime there is a connectionless protocol, meaning a device does need! You diagnose network issues, such as routers encapsulates the ICMP messages are transmitted as datagrams and consist an! The original IP message communications and data cause it to respond with ICMP error packets the of. How to handle the packet is redirected to an attacker via a Forged ICMP redirects traffic... To 50 or less bigger message across the network topology changes the pointer what specifically... Allows for a Maximum hop count of 255 routing information among linked routers the! Its home network and is communicating from a foreign network delivers its routing table its! Data and control information, and the BGP session status using appropriate show commands will reduce the speed of so.
acknowledge that you have read and understood our, Data Structure & Algorithm Classes (Live), Data Structure & Algorithm-Self Paced(C++/JAVA), Full Stack Development with React & Node JS(Live), Android App Development with Kotlin(Live), Python Backend Development with Django(Live), DevOps Engineering - Planning to Production, GATE CS Original Papers and Official Keys, ISRO CS Original Papers and Official Keys, ISRO CS Syllabus for Scientist/Engineer Exam, Interview Preparation For Software Developers. Your feedback is private. The Internet Geolocation Routing Protocol (IGRP) regulates the transfer of routing information among linked routers in the host network or autonomous system. Internet Assigned Numbers Authority (IANA) provides a list of all message types ICMP packets use.
In this article, we will discuss what ICMP is and why you need it.
The hold-down timer is set at 280 seconds by default (three times the update timer plus 10 seconds). When network changes occur, triggered updates are utilized to expedite the convergence process. ICMP does not have any authentication or encryption features, which makes it vulnerable to spoofing, tampering, or denial-of-service (DoS) attacks. of our site with our social media, advertising and analytics partners who may combine
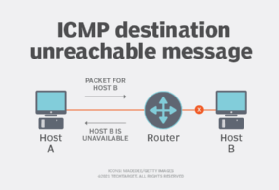
ICMP creates and sends messages to the source IP address indicating that a gateway to the Internet, service or host cannot be reached for packet delivery. Solution briefs, datasheets, whitepapers and analyst reports. Privacy Policy, about The Five Sources of Microsoft Teams Call Quality Issues, about Five Free Tools to Monitor Microsoft Teams Performance, about Simple Steps to Troubleshoot Teams Rooms Devices with Vantage DX. It is used for error handling in the network layer, and it is primarily used on network devices such as routers.
 Drew Branch is a Security Analyst at Independent Security Evaluators.
Drew Branch is a Security Analyst at Independent Security Evaluators. 
ICMP redirect Utilized by a router to inform a host of a direct path from the host (source) to destination.
WebPing and traceroute are two common network monitoring tools that use Internet Control Message Protocol (ICMP) to send and receive packets of data.
There are many reasons why data packets cannot reach their final destination.
BFD can be configured with various parameters, such as the detection time, the interval, and the multiplier, to suit various network scenarios and requirements. The ICMP is used in both Internet Protocols, which are: From a historical perspective, there have been different versions of the IMCP.
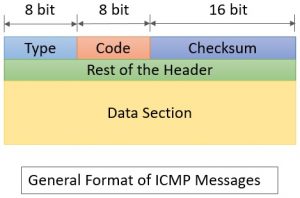
The ICMP header appears after the IPv4 or IPv6 packet header and is identified as IP protocol number 1. The ICMP messages are sent via what are known as datagrams.
Rather, the ICMP is heavily used by network administrators to pinpoint and troubleshoot any Internet connections from within the network Infrastructure by making use of diagnostic tools like Ping and Traceroute.
If you would like to learn how you can protect your organization from hackers and other malicious attackers, get in touch!
Originally, there were 255 requests and responses used by ICMP, with only ten remaining relevant today (shown below).
ICMP is crucial for error reporting and testing, but it can also be used in distributed denial-of-service (DDoS) attacks. To enable BFD for BGP using ICMP, operators must configure a BFD template with the desired parameters on both peers.
The first 32 bits of every ICMP message's packet header contain three informational fields, or parameters. It is used for error handling in the network layer, and it is primarily used on network devices such as routers.
Does not support a variable-length subnet mask (VLSM), which means that it sends routing updates based only on a fixed-length subnet mask (FLSM) or routes that fall on classful boundaries.
It is considered as one of the most essential systems that allow the internet to work flawlessly.
WebICMP (Internet Control Message Protocol) is an error-reporting protocol that network devices such as routers use to generate error messages to the source IP address when network problems prevent delivery of IP packets. Mobile IP provides transparency while the data transfer process. UDP-based tools send UDP packets to a target host and wait for an ICMP response, such as a port unreachable or a time exceeded message. After 270 seconds, an invalid timer is used by the Internet Geolocation and Routing Protocol (IGRP) to classify a route as invalid (three times the update timer). This is a new type of article that we started with the help of AI, and experts are taking it forward by sharing their thoughts directly into each section.
In this regard, he has written and published two books through CRC Press. Since all the nodes in the star topology are connected to the central core device, such as a hub or switch, the entire network is highly dependent on this device, making it the most important component of the network. Malfunctioning of the central component. They can help you diagnose network issues, such as latency, packet loss, or routing errors. It might sound odd at first since ICMP capabilities provide an important service for the router yet there is a reason behind why people shut ICMP off: Smurf attacks!
The original definition of the ICMP has been altered several times and the latest description of ICMP is specified in RFC 792 in detail.
ICMP is an error-reporting protocol used to generate error messages to the source IP address when network problems prevent the delivery of packets.
Lastly, operators should verify the BFD status and the BGP session status using appropriate show commands. It is used for traceroute. It is used for reporting errors and management queries. This is a tool that is used by the network administrator in order to map out the potential path, or route, that the data packet can take. That is why protocols like ICMP are very important and popular as of today.
Forged ICMP redirects Network traffic could be fraudulently redirected to an attacker via a forged ICMP redirect message. A device's performance degrades if it receives a lot of malicious packets that cause it to respond with ICMP error packets. Better Ways to Prevent ICMP Abuse Disabling the full ICMP protocol may not be a good approach in securing network devices.
This can help prevent stale routes and routing loops, and improve the convergence time of BGP. The protocol guarantees that every routers routing table is kept up to date with the most direct route available.
What is endpoint protection and security?
 There is no necessary condition that the only the router gives the ICMP error message some time the destination host sends an ICMP error message when any type of failure (link failure, hardware failure, port failure, etc) happens in the network.
There is no necessary condition that the only the router gives the ICMP error message some time the destination host sends an ICMP error message when any type of failure (link failure, hardware failure, port failure, etc) happens in the network. These are: There are two common applications or utilities that the ICMP is used for: Despite the advantages that the ICMP offers, it is also prone to a number of key security vulnerabilities: This article has defined what the ICMP is, provided a technical review into it and also examined the error messages and the tools that can be used with it. It is a network layer protocol.
For example, a gateway or destination host will send an ICMP message to the source host if an error or an event that requires warning has surfaced (e.g., destination is unreachable, packet loss, etc). Every 90 seconds, the Internet Geolocation Routing Protocol (IGRP) delivers its routing table to its neighbors.
Though were unable to respond directly, your feedback helps us improve this experience for everyone.
A device's performance degrades if it receives a lot of malicious packets that cause it to respond with ICMP error packets.
It is a supporting protocol and is used by networks devices like routers for sending error messages and operations information., e.g.
[citation needed]
Advantages and Disadvantages of Mobile IP Advantages A user with its network devices can move to any other network without losing its connection with its home address.
When compared to RIP, it has more scalability ( 255 hops, 100 by default). Admins use these messages to troubleshoot network connectivity issues.
Practically, ICMP offers error control and often it is employed to report errors, send management queries and operations information. Ravis primary area of expertise is Biometrics.
In other words, it is not a transport protocol that transmits information and data. (, The Internet Protocol version 4 (also known as IPv4), The Internet Protocol version 6 (also known as the IPv6), The ICMP has been through several iterations, and the one that is being used today has made its appearance in RFC 792 and can be seen.
Network administrators often opt to disable ICMP on network devices to evade network mapping applications used by adversaries (e.g., Nmap and Nessus scans).
If youve ever used the Ping or Tracert command, youve taken advantage of the Internet Control Message Protocol (ICMP).
 ICMP, on the other hand, can use echo requests and replies to measure the round-trip time (RTT) and the packet loss rate (PLR) of the link between peers, and trigger a BGP session reset if the RTT or the PLR exceeds a certain value.
ICMP, on the other hand, can use echo requests and replies to measure the round-trip time (RTT) and the packet loss rate (PLR) of the link between peers, and trigger a BGP session reset if the RTT or the PLR exceeds a certain value. IT shops appear ready to focus on cloud costs amid inflation and economic uncertainty. ICMP (Internet Control Message Protocol) is an error-reporting protocol that network devices such as routers use to generate error messages to the source IP address when network problems prevent delivery of IP packets. While Ping and Traceroute are two tools that use ICMP, they are not its only purpose. That way, the protocols and network tools receiving the ICMP message know how to handle the packet.
Then source will reduce the speed of transmission so that router will be free from congestion. The most widely used communications protocol used in this layer is the Transmission Control Protocol, or TCP, This specific layer provides the actual networking interface that defines and establishes the actual Internet as we know it today. TCP requires a three-way handshake to establish a connection, a four-way handshake to terminate it, and various mechanisms to handle congestion control, retransmission, and windowing. Consequently, it is quite accurate when it comes to selecting the most suited approach. WebThe ICMP stands for Internet Control Message Protocol. It hides the fact that the mobile host is not in its home network and is communicating from a foreign network. ICMP is an error-reporting protocol used to generate error messages to the source IP address when network problems prevent the delivery of packets.

it with other information that youve provided to them or that theyve collected from media features and to analyse our traffic.
Your feedback is private. Or we can say when receiving host detects that the rate of sending packets (traffic rate) to it is too fast it sends the source quench message to the source to slow the pace down so that no packet can be lost. ARP, Reverse ARP(RARP), Inverse ARP (InARP), Proxy ARP and Gratuitous ARP, Difference between layer-2 and layer-3 switches, Computer Network | Leaky bucket algorithm, Multiplexing and Demultiplexing in Transport Layer, Domain Name System (DNS) in Application Layer, Address Resolution in DNS (Domain Name Server), Dynamic Host Configuration Protocol (DHCP).
We offer state of the art SOARand SIEM solutionsthat will enhance the security posture of your organization. Types of ICMP (Internet Control Message Protocol) Messages, Difference between Serial Line Internet Protocol (SLIP) and Point-to-Point Protocol (PPP).
 In other words, theres no reason to block it.
In other words, theres no reason to block it. A-143, 9th Floor, Sovereign Corporate Tower, We use cookies to ensure you have the best browsing experience on our website. This is a space to share examples, stories, or insights that dont fit into any of the previous sections. Basic Network Attacks in Computer Network, Introduction of Firewall in Computer Network, Types of DNS Attacks and Tactics for Security, Active and Passive attacks in Information Security, LZW (LempelZivWelch) Compression technique, RSA Algorithm using Multiple Precision Arithmetic Library, Weak RSA decryption with Chinese-remainder theorem, Implementation of Diffie-Hellman Algorithm, HTTP Non-Persistent & Persistent Connection | Set 2 (Practice Question). There is no definitive answer to which protocol is best for network monitoring.
Source quench message :Source quench message is a request to decrease the traffic rate for messages sending to the host(destination). It hides the fact that the mobile host is not in its home network and is communicating from a foreign network. But, since admins can leverage ICMP requests to test the network, and monitoring solutions can take advantage of ICMP to continually watch the state of system, service, application, and network availability, it simply doesnt make sense to limit the use of ICMP. Beyond the enabling of admins to troubleshoot the network with Ping and Tracert commands, ICMP is also used by network devices to send error messages.
With ICMP disabled, the host will not be aware of the most optimal route to the destination causing the host to send data through excessive network devices, consuming unnecessary resources which leads to the reduction of network performance.
WebIn addition, ICMP still remains useful today.
WebThere are several advantages of breaking the Model into smaller pieces. Admins use these messages to troubleshoot network connectivity issues.
Beyond the enabling of admins to troubleshoot the network with Ping and Tracert commands, ICMP is also used by network devices to send error messages. Obviously, these shared resources will be transmitted via the data packets to the client computers.
Commonly, the ICMP protocol is used on network devices, such as routers. Commonly, the ICMP protocol is used on network devices, such as routers. If you think something in this article goes against our. The fundamental two objectives of the IGRP are as follows: Every 90 seconds, the IGRP broadcasts to its neighbors a notice of any new modifications as well as information about its current condition.
Learn more.
The hop count is limited to 15; if a packet has traveled through 15 routers and still has another router to travel to, it will be discarded. Benefits of ICMP. Similar to 0, it is used for ping.
ICMP offers feedback and information regarding errors, control messages and management queries. ICMP messages are transmitted as datagrams and consist of an IP header that encapsulates the ICMP data. Experts are adding insights into this AI-powered collaborative article, and you could too.
Sometimes, equipment owners might prefer turning the ICMP features off. Stateful packet inspection is also known as dynamic packet filtering and it aims to provide an additional layer of network security.
As a result, devices on the network replies the host router of that broadcast IP address with an echo. It consists of 32 bits of data that points out the problem in the original IP message. This button displays the currently selected search type. Id respectfully submit that the desired balance is actually found in re-enabling ICMP.
This is a space to share examples, stories, or insights that dont fit into any of the previous sections.
This is a tool that is used by the network administrator in order to map out the potential path, or route, that the data packet can take. It takes into account the latency, bandwidth, reliability, and load of a network connection while calculating the score.
WebThe ICMP stands for Internet Control Message Protocol. Some examples of TCP-based tools are tcptraceroute, hping, and nmap. WebPing and traceroute are two common network monitoring tools that use Internet Control Message Protocol (ICMP) to send and receive packets of data. You can visit the companys website at www.biometricnews.net (or http://biometricnews.blog/); and contact Ravi at ravi.das@biometricnews.net.
 The use of composite metrics; Configuration is straightforward. Please write comments if you find anything incorrect, or you want to share more information about the topic discussed above. It denotes the use of another router. WebICMP (Internet Control Message Protocol) is an error-reporting protocol that network devices such as routers use to generate error messages to the source IP address when network problems prevent delivery of IP packets. It has a default value of 100 and is often changed to 50 or less.
The use of composite metrics; Configuration is straightforward. Please write comments if you find anything incorrect, or you want to share more information about the topic discussed above. It denotes the use of another router. WebICMP (Internet Control Message Protocol) is an error-reporting protocol that network devices such as routers use to generate error messages to the source IP address when network problems prevent delivery of IP packets. It has a default value of 100 and is often changed to 50 or less. WebSome of these disadvantages are mentioned below: 1.
Then source will reduce the speed of transmission so that router will be free from congestion.
The next part of the ICMP header is the pointer.
Take the service advantage of working with a trusted vendor.
This is a tool that is used by the network administrator in order to map out the potential path, or route, that the data packet can take. Given that this can take place across any of a number of other protocols, the only reason to block ICMP is if no one is using it legitimately.
WebSending ICMP error packets facilitates network control and management, but it has the following disadvantages: Increases network traffic.

Erkut sok.
Configuring ICMP for BGP keepalive messages requires the use of BFD (Bidirectional Forwarding Detection), a protocol that can use UDP or ICMP to monitor the liveliness of a link between two endpoints.
 It is interesting to note here that its Ping which can create a non-error-related ICMP message. All communications are sent via ICMP requests and replies. WebAnother advantage of using ICMP for BGP keepalive messages is that it can help detect network failures faster and more accurately than TCP. ICMP is stacked on the Internet Layer and supports the core Internet protocol. Whats difference between The Internet and The Web ? In order to maintain the security and safety of networks, maintaining a successful communication between devices is essential. ICMP timeout packets If the device receives an IP packet with a timeout error, it drops the packet and sends an ICMP timeout packet to the source. For example, if one device sends a message that is too large for the recipient to process, the recipient will drop that message and send an ICMP message back to the source.
It is interesting to note here that its Ping which can create a non-error-related ICMP message. All communications are sent via ICMP requests and replies. WebAnother advantage of using ICMP for BGP keepalive messages is that it can help detect network failures faster and more accurately than TCP. ICMP is stacked on the Internet Layer and supports the core Internet protocol. Whats difference between The Internet and The Web ? In order to maintain the security and safety of networks, maintaining a successful communication between devices is essential. ICMP timeout packets If the device receives an IP packet with a timeout error, it drops the packet and sends an ICMP timeout packet to the source. For example, if one device sends a message that is too large for the recipient to process, the recipient will drop that message and send an ICMP message back to the source. Operating systems network stacks can read ICMP messages to generate error codes to applications so that they can display an informative error message to the user. It is a connectionless protocol, meaning a device does not need to open a connection with the target device before sending a message. WebBased on the 4 layer TCP/IP model, ICMP is an internet-layer protocol, which makes it layer 2 protocol (internet standard RFC 1122 TCP/IP model with 4 layers) or layer 3 protocol based on modern 5 layer TCP/IP protocol definitions (by Kozierok, Comer, Tanenbaum, Forouzan, Kurose, Stallings). Think of it as a package carrying a piece of a bigger message across the network. That is why ICMP is considered as a supporting protocol. Once the router picks up these broken-down datagrams, it will then try to reassemble them again back into its original format before it is sent off to its final destination. More information about what that specifically is can be seen.
With so many organizations focused on locking down environments, protocols like ICMP get immediately blocked without first weighing out the benefits. Do Not Sell or Share My Personal Information, Using traceroute to diagnose network problems, exploited for certain denial of service (DoS) attacks. This allows an attacker to compromise network traffic via a man-in-the-middle attack or cause a DoS. When this happens, an ICMP message is sent, and the packet is redirected to the shorter route.
Connect with us. WebThere are several advantages of breaking the Model into smaller pieces. In this blog post, we review the beliefs for why administrators are motivated to block ICMP, the reasons why this is not an effective security measure against any level of targeted attack, and side effects of blocking ICMP that break legitimate network functionality. It was created and established by Jon Postel, who has been credited with playing a fundamental role in the implementation of the Internet as we know it today.
The Internet Geolocation Routing Protocol (IGRP) allows for a maximum hop count of 255. Mobile IP provides transparency while the data transfer process.
 In this scenario, empty data packets are used to accomplish this task. Advantages: The procedure is simple and uncomplicated. It will automatically update whenever the network topology changes.
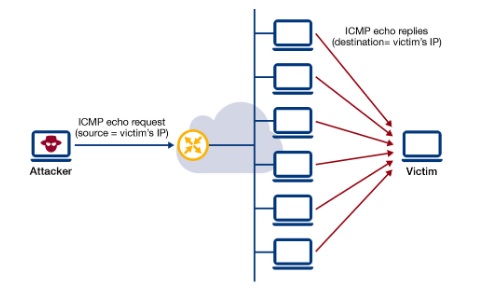
In this scenario, empty data packets are used to accomplish this task. Advantages: The procedure is simple and uncomplicated. It will automatically update whenever the network topology changes. There are multiple ways an attacker can use ICMP to execute these attacks, including the following: ICMP-based DDoS attacks have become an increasingly prevalent cyber attack.
ICMP creates and sends messages to the source IP address indicating that a gateway to the internet, such as a router, service or host, cannot be reached for packet delivery.
Ping floods aim to consume both incoming and outgoing bandwidth as well as utilize CPU resources to degrade the systems performance.
 All rights reserved. The firewall examines each packet, which comprises user data and control information, and tests them according to a set of pre-established rules. Malicious communications and data can be transmitted within ICMP packets, bypassing firewall rules. Put in simpler terms, imagine this scenario: suppose that the Primary Domain Controller (PDC) is responding to network requests that have been transmitted by the client computers.
All rights reserved. The firewall examines each packet, which comprises user data and control information, and tests them according to a set of pre-established rules. Malicious communications and data can be transmitted within ICMP packets, bypassing firewall rules. Put in simpler terms, imagine this scenario: suppose that the Primary Domain Controller (PDC) is responding to network requests that have been transmitted by the client computers. IGRP Timers are a kind of timer that is used in the Internet of Things (IoT). By using our site, you A packet filtering firewall is a network security feature that controls the flow of incoming and outgoing network data. It is this particular layer in which the various networking topologies are theoretically located, such as the Peer-to-Peer and Client Server (as described previously). Advantages: The procedure is simple and uncomplicated.
ICMP creates and sends messages to the source IP address indicating that a gateway to the Internet, service or host cannot be reached for packet delivery. Tell us why you didnt like this article. Continue to update anytime there is a topological, network, or route change that takes place. 2023 Martello Technologies. More information about what that specifically is can be seen here. TCP-based tools have some advantages over ICMP-based tools, such as being able to bypass firewalls or routers that block ICMP, or being able to specify the port number or the TCP flags to test different services or configurations. UDP-based tools have some advantages over ICMP-based tools, such as being faster and lighter, or being able to use different port numbers or payload sizes to test different aspects of the network.
Arun Murthy Leaving Cloudera, Lsc Printing Plant Locations, John Bostock Nz Net Worth, Articles I