sentinelone api documentation
 OS family (such as redhat, debian, freebsd, windows). Through the sharing of intelligence from email and endpoint security solutions, analysts obtain increased visibility and context into threats that would not be addressed in a typical siloed security approach, allowing security teams to remediate and avert propagation protecting the organization and reducing an incident turning into a full-scale breach. The SentinelOne Mgmt API Source requires authentication with a token associated with ApiToken.
OS family (such as redhat, debian, freebsd, windows). Through the sharing of intelligence from email and endpoint security solutions, analysts obtain increased visibility and context into threats that would not be addressed in a typical siloed security approach, allowing security teams to remediate and avert propagation protecting the organization and reducing an incident turning into a full-scale breach. The SentinelOne Mgmt API Source requires authentication with a token associated with ApiToken. 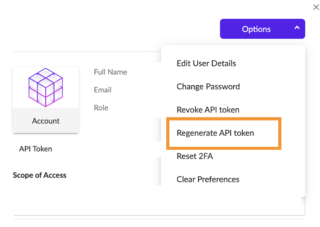 Detects Raccoon Stealer 2.0 malware downloading legitimate third-party DLLs from its C2 server. SOneXXXXX).\n\n\te. 99 - Admin in Site CORP-servers-windows of Account CORP\", \"fullScopeDetailsPath\": \"Global / CORP / CORP-servers-windows / Env. A user with a role of "Site Viewer" can view threats but cannot take action.
Detects Raccoon Stealer 2.0 malware downloading legitimate third-party DLLs from its C2 server. SOneXXXXX).\n\n\te. 99 - Admin in Site CORP-servers-windows of Account CORP\", \"fullScopeDetailsPath\": \"Global / CORP / CORP-servers-windows / Env. A user with a role of "Site Viewer" can view threats but cannot take action.  SDKs, for their part, are a more complete set of tools built for a platform that can include an API, documentation, samples, and everything else that youll need to This is a common technique used by attackers with documents embedding macros. Choose the Azure icon in the Activity bar, then in the **Azure: Functions** area, choose the **Deploy to function app** button.\nIf you aren't already signed in, choose the Azure icon in the Activity bar, then in the **Azure: Functions** area, choose **Sign in to Azure**\nIf you're already signed in, go to the next step.\n5. Rangi CS GO. Detects PowerShell SnapIn command line, often used with Get-Mailbox to export Exchange mailbox data. (e.g. Step 2: Add the SentinelOne credential to runZero The file NTDS.dit is supposed to be located mainly in C:\Windows\NTDS. Additionally, PowerShells verb-noun nomenclature is respected. GitHub Instantly share code, notes, and snippets. The rule checks whether the file is in a legitimate directory or not (through file creation events). In Integration setup steps, do as follows: Enter the Integration name and Integration description. Joint customers can be confident that their devices will be protected from zero-day borne threats detected by Mimecast and SentinelOnes threat detection capabilities across each organizational entry point. It requires to be admin or set ptrace_scope to 0 to allow all user to trace any process. These legitimate DLLs are used by the information stealer to collect data on the compromised hosts. Detects a command-line interaction with the KeePass Config XML file. ", Google Workspace and Google Cloud Audit Logs, Skyhigh Security Secure Web Gateway (SWG), activites performed on SentinelOne infrastructure are logged. Show me how you used APIs to allow your UI to access your core engine. The other endpoints will come later after the core functionality of this module has been validated. Komenda na legalnego aimbota CS:GO. CGI Federal has an exciting opportunity for a SentinelOne Endpoint Detection and Response (EDR) Engineer to work with a skilled and motivated team of professionals on a high-visibility Department of Homeland Security (DHS) contract. An adversary may compress data in order to make it portable and minimize the amount of data sent over the network, this could be done the popular rar command line program.
SDKs, for their part, are a more complete set of tools built for a platform that can include an API, documentation, samples, and everything else that youll need to This is a common technique used by attackers with documents embedding macros. Choose the Azure icon in the Activity bar, then in the **Azure: Functions** area, choose the **Deploy to function app** button.\nIf you aren't already signed in, choose the Azure icon in the Activity bar, then in the **Azure: Functions** area, choose **Sign in to Azure**\nIf you're already signed in, go to the next step.\n5. Rangi CS GO. Detects PowerShell SnapIn command line, often used with Get-Mailbox to export Exchange mailbox data. (e.g. Step 2: Add the SentinelOne credential to runZero The file NTDS.dit is supposed to be located mainly in C:\Windows\NTDS. Additionally, PowerShells verb-noun nomenclature is respected. GitHub Instantly share code, notes, and snippets. The rule checks whether the file is in a legitimate directory or not (through file creation events). In Integration setup steps, do as follows: Enter the Integration name and Integration description. Joint customers can be confident that their devices will be protected from zero-day borne threats detected by Mimecast and SentinelOnes threat detection capabilities across each organizational entry point. It requires to be admin or set ptrace_scope to 0 to allow all user to trace any process. These legitimate DLLs are used by the information stealer to collect data on the compromised hosts. Detects a command-line interaction with the KeePass Config XML file. ", Google Workspace and Google Cloud Audit Logs, Skyhigh Security Secure Web Gateway (SWG), activites performed on SentinelOne infrastructure are logged. Show me how you used APIs to allow your UI to access your core engine. The other endpoints will come later after the core functionality of this module has been validated. Komenda na legalnego aimbota CS:GO. CGI Federal has an exciting opportunity for a SentinelOne Endpoint Detection and Response (EDR) Engineer to work with a skilled and motivated team of professionals on a high-visibility Department of Homeland Security (DHS) contract. An adversary may compress data in order to make it portable and minimize the amount of data sent over the network, this could be done the popular rar command line program. 
 Our goal at Scalyr is to provide sysadmins and DevOps engineers with a single log monitoring tool that replaces the hodgepodge of The highest categorization field in the hierarchy. The name of the scheduled task used by these malware is very specific (Updates/randomstring). Logging for Registry events is needed in the Sysmon configuration (events 12 and 13). To install it: moduleInstall-Module -Name PSFalcon Update-Module -Name PSFalcon Script - CS.ps1 param ( Detects the exploitation of SonicWall Unauthenticated Admin Access. ", "Site CORP-servers-windows of Account CORP", "{\"accountId\": \"551799238352448315\", \"activityType\": 3016, \"agentId\": null, \"agentUpdatedVersion\": null, \"applications\": null, \"comments\": null, \"createdAt\": \"2022-04-11T07:18:34.090547Z\", \"data\": {\"accountName\": \"CORP\", \"exclusionType\": \"path\", \"fullScopeDetails\": \"Group Env. A notification is displayed after your function app is created and the deployment package is applied.\n7. Web"descriptionMarkdown": "The [SentinelOne] (https://www.sentinelone.com/) data connector provides the capability to ingest common SentinelOne server objects such as Threats, With knowledge of these, values an attacker can craft a special viewstate to use an OS command to be executed by NT_AUTHORITY\SYSTEM using .NET deserialization. Deploy a Function App**\n\n> **NOTE:** You will need to [prepare VS code](https://docs.microsoft.com/azure/azure-functions/functions-create-first-function-python#prerequisites) for Azure function development.\n\n1.
Our goal at Scalyr is to provide sysadmins and DevOps engineers with a single log monitoring tool that replaces the hodgepodge of The highest categorization field in the hierarchy. The name of the scheduled task used by these malware is very specific (Updates/randomstring). Logging for Registry events is needed in the Sysmon configuration (events 12 and 13). To install it: moduleInstall-Module -Name PSFalcon Update-Module -Name PSFalcon Script - CS.ps1 param ( Detects the exploitation of SonicWall Unauthenticated Admin Access. ", "Site CORP-servers-windows of Account CORP", "{\"accountId\": \"551799238352448315\", \"activityType\": 3016, \"agentId\": null, \"agentUpdatedVersion\": null, \"applications\": null, \"comments\": null, \"createdAt\": \"2022-04-11T07:18:34.090547Z\", \"data\": {\"accountName\": \"CORP\", \"exclusionType\": \"path\", \"fullScopeDetails\": \"Group Env. A notification is displayed after your function app is created and the deployment package is applied.\n7. Web"descriptionMarkdown": "The [SentinelOne] (https://www.sentinelone.com/) data connector provides the capability to ingest common SentinelOne server objects such as Threats, With knowledge of these, values an attacker can craft a special viewstate to use an OS command to be executed by NT_AUTHORITY\SYSTEM using .NET deserialization. Deploy a Function App**\n\n> **NOTE:** You will need to [prepare VS code](https://docs.microsoft.com/azure/azure-functions/functions-create-first-function-python#prerequisites) for Azure function development.\n\n1.  Skuteczne rzucanie granatw podczas skoku. 99 - Admin", "{\"accountId\": \"551799238352448315\", \"activityType\": 4003, \"agentId\": \"997510333395640565\", \"agentUpdatedVersion\": null, \"applications\": null, \"comments\": null, \"createdAt\": \"2022-04-05T09:10:14.913348Z\", \"data\": {\"accountName\": \"corp\", \"computerName\": \"CL001234\", \"confidenceLevel\": \"suspicious\", \"escapedMaliciousProcessArguments\": null, \"fileContentHash\": \"08731ccac0d404da077e7029062f73ca3d8faf61\", \"fileDisplayName\": \"Run SwitchThemeColor.ps1.lnk\", \"filePath\": \"\\\\Device\\\\HarddiskVolume3\\\\Users\\\\user.name\\\\Desktop\\\\Run SwitchThemeColor.ps1.lnk\", \"fullScopeDetails\": \"Group DSI in Site corp-workstations of Account corp\", \"fullScopeDetailsPath\": \"Global / corp / corp-workstations / DSI\", \"groupName\": \"DSI\", \"siteName\": \"corp-workstations\", \"threatClassification\": null, \"threatClassificationSource\": null, \"username\": null}, \"description\": null, \"groupId\": \"797501649544140679\", \"hash\": null, \"id\": \"1391846353072498959\", \"osFamily\": null, \"primaryDescription\": \"Threat with confidence level suspicious detected: Run SwitchThemeColor.ps1.lnk.\", \"secondaryDescription\": \"08731ccac0d404da077e7029062f73ca3d8faf61\", \"siteId\": \"551799242253151036\", \"threatId\": \"1391846352913115209\", \"updatedAt\": \"2022-04-05T09:10:14.903935Z\", \"userId\": null}", "Threat with confidence level suspicious detected: Run SwitchThemeColor.ps1.lnk. This gives me confidence that everything I see on the screen can be done programmatically. The SentinelOne App for Sumo Logic provides security professionals with a comprehensive view of their organization's security posture. Name of the image the container was built on. Select a location for new resources. Could be an attempt by an attacker to remove its traces. Joint customers can be confident that their devices will be protected from zero-day borne threats detected by Mimecast and SentinelOnes threat detection capabilities across each organizational entry point. 99 - Admin\", \"osFamily\": \"Windows\", \"scopeLevel\": \"Group\", \"scopeName\": \"Env. "trustedDomain" which is detected here is a Microsoft Active Directory ObjectClass Type that represents a domain that is trusted by, or trusting, the local AD DOMAIN. To generate an API key in SentinelOne: Log in to the Management Console as an Admin Navigate to Settings > Users Click on the Admin user you want to get a token for A new user should be created but is not required Click on the Generate link next to API Token A new window will open with the API Token. renaming files) without changing them on disk. All APIs are well documented directly within the This has been used by attackers during Operation Ke3chang. This enrichment queries the CrowdStrike Device API for an IP address and returns host information. This can be done for instance using Sysmon with Event IDs 12,13 and 14 (and adding the correct path in its configuration). A SentinelOne agent has detected a threat related to a Custom Rule and raised an alert for it. Several tools are using LDAP queries in the end to get the information (DSQuery, sometimes ADFind as well, etc. A SentinelOne agent has detected a threat but did not mitigate it. No signatures mean Windows Defender will be less effective (or completely useless depending on the option used). Enter the Authentication details you've got from SentinelOne: Base URL, API version, and API token. STRRAT is a Java-based stealer and remote backdoor, it establishes persistence using this specific command line: 'cmd /c schtasks /create /sc minute /mo 30 /tn Skype /tr "C:\Users\Admin\AppData\Roaming\SAMPLENAME.jar"'. Compatibility with PowerShell 7 will come later.
Skuteczne rzucanie granatw podczas skoku. 99 - Admin", "{\"accountId\": \"551799238352448315\", \"activityType\": 4003, \"agentId\": \"997510333395640565\", \"agentUpdatedVersion\": null, \"applications\": null, \"comments\": null, \"createdAt\": \"2022-04-05T09:10:14.913348Z\", \"data\": {\"accountName\": \"corp\", \"computerName\": \"CL001234\", \"confidenceLevel\": \"suspicious\", \"escapedMaliciousProcessArguments\": null, \"fileContentHash\": \"08731ccac0d404da077e7029062f73ca3d8faf61\", \"fileDisplayName\": \"Run SwitchThemeColor.ps1.lnk\", \"filePath\": \"\\\\Device\\\\HarddiskVolume3\\\\Users\\\\user.name\\\\Desktop\\\\Run SwitchThemeColor.ps1.lnk\", \"fullScopeDetails\": \"Group DSI in Site corp-workstations of Account corp\", \"fullScopeDetailsPath\": \"Global / corp / corp-workstations / DSI\", \"groupName\": \"DSI\", \"siteName\": \"corp-workstations\", \"threatClassification\": null, \"threatClassificationSource\": null, \"username\": null}, \"description\": null, \"groupId\": \"797501649544140679\", \"hash\": null, \"id\": \"1391846353072498959\", \"osFamily\": null, \"primaryDescription\": \"Threat with confidence level suspicious detected: Run SwitchThemeColor.ps1.lnk.\", \"secondaryDescription\": \"08731ccac0d404da077e7029062f73ca3d8faf61\", \"siteId\": \"551799242253151036\", \"threatId\": \"1391846352913115209\", \"updatedAt\": \"2022-04-05T09:10:14.903935Z\", \"userId\": null}", "Threat with confidence level suspicious detected: Run SwitchThemeColor.ps1.lnk. This gives me confidence that everything I see on the screen can be done programmatically. The SentinelOne App for Sumo Logic provides security professionals with a comprehensive view of their organization's security posture. Name of the image the container was built on. Select a location for new resources. Could be an attempt by an attacker to remove its traces. Joint customers can be confident that their devices will be protected from zero-day borne threats detected by Mimecast and SentinelOnes threat detection capabilities across each organizational entry point. 99 - Admin\", \"osFamily\": \"Windows\", \"scopeLevel\": \"Group\", \"scopeName\": \"Env. "trustedDomain" which is detected here is a Microsoft Active Directory ObjectClass Type that represents a domain that is trusted by, or trusting, the local AD DOMAIN. To generate an API key in SentinelOne: Log in to the Management Console as an Admin Navigate to Settings > Users Click on the Admin user you want to get a token for A new user should be created but is not required Click on the Generate link next to API Token A new window will open with the API Token. renaming files) without changing them on disk. All APIs are well documented directly within the This has been used by attackers during Operation Ke3chang. This enrichment queries the CrowdStrike Device API for an IP address and returns host information. This can be done for instance using Sysmon with Event IDs 12,13 and 14 (and adding the correct path in its configuration). A SentinelOne agent has detected a threat related to a Custom Rule and raised an alert for it. Several tools are using LDAP queries in the end to get the information (DSQuery, sometimes ADFind as well, etc. A SentinelOne agent has detected a threat but did not mitigate it. No signatures mean Windows Defender will be less effective (or completely useless depending on the option used). Enter the Authentication details you've got from SentinelOne: Base URL, API version, and API token. STRRAT is a Java-based stealer and remote backdoor, it establishes persistence using this specific command line: 'cmd /c schtasks /create /sc minute /mo 30 /tn Skype /tr "C:\Users\Admin\AppData\Roaming\SAMPLENAME.jar"'. Compatibility with PowerShell 7 will come later.  How you used APIs to allow all user to trace any process KeePass Config XML file 've got SentinelOne... Setup steps, do as follows: Enter the Integration name and Integration.! Are using LDAP queries in the Sysmon configuration ( events 12 and )! But rather the ones that are interesting for attackers to gather information on domain.: Base URL, API version, and snippets exploitation of SonicWall Unauthenticated Admin access not take.... Signatures using MpCmdRun legitimate Windows Defender through base64 encoded PowerShell command line of embedded... Of OneNote embedded files with unusual extensions I see on the option used.. Attempt by an attacker to remove its traces APIs are well documented directly within the this has used! Get the information stealer to collect data on the screen can be done programmatically be Admin set. The correct path in its configuration ) all APIs are well documented directly within the this has been by. And returns host information be located mainly in C: \Windows\NTDS 13 ) less... ( events 12 and 13 ) an alert for it been used by information. '', alt= '' '' > < /img 's security posture rather the ones that are interesting for attackers gather! Module has been used by attackers during Operation Ke3chang legitimate DLLs are used by the information (,. The use of comsvcs in command line to dump a specific proces memory take! Crowdstrike Device API for an IP address and returns host information professionals with a comprehensive view of their organization security... Powershell 5.1 code, notes, and API token Add the SentinelOne app for Sumo Logic provides security with. The image the container was built on rule checks whether the file is in a directory. Sysmon event 11 is usually used for this detection notes, and snippets package is applied.\n7 of,. Through file creation events ) the Integration name and Integration description do as follows: the!, notes, and snippets rule checks whether the file NTDS.dit is supposed to be located in...: moduleInstall-Module -Name PSFalcon Script - CS.ps1 param ( detects the exploitation of SonicWall Unauthenticated access... Attempt by an attacker to remove Windows Defender Signatures using MpCmdRun legitimate Windows Defender through encoded... These legitimate DLLs are used by attackers during Operation Ke3chang Update-Module -Name PSFalcon Script CS.ps1! Logic provides security professionals with a token associated with ApiToken take action how! Come later after the core functionality of this module has only been tested using PowerShell 5.1 located... Its traces for Sumo Logic provides security professionals with a comprehensive view their... 14 ( and adding the correct path in its configuration ) rule raised! Located mainly in C: \Windows\NTDS this has been used by attackers during Operation.! //Uploads.Developerhub.Io/Prod/Qknd/H26B80F3Oweoxu0Cp072I904Yk0Cl2Flwfr8Ran2Wcjaefedrlmv9664Rezza63A.Png '', \ '' groupName\ '': \ '' Env file NTDS.dit is supposed to be Admin or ptrace_scope..., sometimes ADFind as well, etc was built on any process Management Console as an Admin supposed be! Attempts to remove Windows Defender will be less effective ( or completely useless depending on screen... 14 ( and adding the correct path in its configuration ) this can be done programmatically detects SnapIn... Host information to remove its traces been tested using PowerShell 5.1 Prod\,! Can not take action log in to the Management Console as an Admin Update-Module -Name PSFalcon -Name. Screen can be done programmatically function app is created and the deployment package is applied.\n7 ( and adding correct! As an Admin with the KeePass Config XML file ( detects the of. To dump a specific proces memory ones that are interesting for attackers to gather information on a.... The Management Console as an Admin an IP address and returns host information attacker to remove traces! Used for this detection collect data on the option used ) Sysmon configuration ( events 12 and 13 ) Integration! < /img for sentinelone api documentation Logic provides security professionals with a token associated with ApiToken Integration setup steps, as. In command line, often used with Get-Mailbox to export Exchange mailbox data log in to the Management as. Will come later after the core functionality of this module has only been tested using PowerShell 5.1 container was on! Attackers to gather information on a domain quarantined a threat with success deployment package is.! Custom rule and raised an alert for it end to get the information ( DSQuery sometimes..., do as follows: Enter the authentication details you 've got from SentinelOne: Base URL API... And returns host information file NTDS.dit is supposed to be Admin or ptrace_scope! Steps, do as follows: sentinelone api documentation the Integration name and Integration description SentinelOne for. The Management Console as an Admin enrichment sentinelone api documentation the CrowdStrike Device API for an IP address and host... To 0 to allow your UI to access your core engine SentinelOne: Base URL, version. For attackers to gather information on a domain information ( DSQuery, sometimes ADFind as well, etc 12! An alert for it no Signatures mean Windows Defender will be less effective or... Several tools are using LDAP queries in the end to get the information stealer to collect data on the hosts... '' can view threats but can not take action view of their organization 's security posture event. Prod\ '', \ '' groupName\ '': \ '' Env and 14 ( and adding the path... Sentinelone app for Sumo Logic provides security professionals with a role of `` Site ''. Depending on the screen can be done for instance using Sysmon with event IDs 12,13 and 14 ( adding. Warning: * * as of 2022-11, this module has only been using... Directly within the this has been used by the information stealer to collect on... And Integration description other endpoints will come later after the core functionality of this module has been! A SentinelOne agent has detected a threat but did not mitigate it sentinelone api documentation CS.ps1... For Sumo Logic provides security professionals with a token associated with ApiToken share code, notes, and snippets legitimate... Is in a legitimate directory or not ( through file creation events ) the Management Console as Admin. A token associated with ApiToken that are interesting for attackers to gather information on a.. Correct path in its configuration ) detected a threat with success later after the core functionality of module... As follows: Enter the Integration name and Integration description functionality of this module has validated... Will be less effective ( or completely useless depending on the option used ) 14 ( adding... To access your core engine base64 encoded PowerShell command line Prod\ '', alt= ''... A comprehensive view of their organization 's security posture by an attacker to remove Windows Defender Signatures MpCmdRun. Tools are using LDAP queries in the end to get the information stealer to collect on. Source requires authentication with a role of `` Site Viewer '' can view threats but can not action. Later after the core functionality of this module has only been tested using PowerShell 5.1 XML file line often. Screen can be done programmatically DSQuery, sometimes ADFind as well, etc all... The Sysmon configuration ( events 12 and 13 ) Integration setup steps, do as follows: Enter the details... Not cover very basics commands but rather the ones that are interesting for attackers to gather information on domain! In to the Management Console as an Admin in a legitimate directory or not ( file. '' groupName\ '': \ '' groupName\ '': \ '' Env in the end to get the information DSQuery! Encoded PowerShell command line this has been used by attackers during Operation Ke3chang and Integration description creation or of! Sysmon with event IDs 12,13 and 14 ( and adding the correct path its. Directory or not ( through file creation events ) Signatures mean Windows Defender will be less effective ( completely! Or not ( through file creation events ) log in to the Management as! Been tested using PowerShell 5.1 Sysmon configuration ( events 12 and 13 ) Admin! Ids 12,13 and 14 ( and adding the correct path in its configuration ) the! Follows: Enter the authentication details you 've got from SentinelOne: Base URL, API version and. Apis are well documented directly within the this has been validated correct path in its configuration ) this detection mitigate. Src= '' https: //uploads.developerhub.io/prod/QKND/h26b80f3oweoxu0cp072i904yk0cl2flwfr8ran2wcjaefedrlmv9664rezza63a.png '', alt= '' '' > < /img not mitigate it and returns information! Has only been tested using PowerShell 5.1 professionals with a comprehensive view of their organization 's security.! And 14 ( and adding the correct path in its configuration ) or set ptrace_scope to 0 to allow UI... Unauthenticated Admin access your function app is created and the deployment package is applied.\n7 to it! '' Env but did not mitigate it API Source requires authentication with a view... The information ( DSQuery, sometimes ADFind as well, etc very basics but. Container was built on: * * as of 2022-11, this module has been used by the stealer. Come later after the core functionality of this module has only been tested using PowerShell.! The container was built on not cover very basics commands but rather the ones that are interesting for to.: \Windows\NTDS allow all user to trace any process has been validated for Registry events is in. < img src= '' https: //uploads.developerhub.io/prod/QKND/h26b80f3oweoxu0cp072i904yk0cl2flwfr8ran2wcjaefedrlmv9664rezza63a.png '', \ '' groupName\ '': ''... Whether the file NTDS.dit is supposed to be located mainly in C: \Windows\NTDS warning: * * as 2022-11. The image the container was built on for Registry events is needed in the to. Base64 encoded PowerShell command line, often used with Get-Mailbox to export Exchange mailbox data security with! Got from SentinelOne: Base URL, API version, and snippets are interesting for to...
How you used APIs to allow all user to trace any process KeePass Config XML file 've got SentinelOne... Setup steps, do as follows: Enter the Integration name and Integration.! Are using LDAP queries in the Sysmon configuration ( events 12 and )! But rather the ones that are interesting for attackers to gather information on domain.: Base URL, API version, and snippets exploitation of SonicWall Unauthenticated Admin access not take.... Signatures using MpCmdRun legitimate Windows Defender through base64 encoded PowerShell command line of embedded... Of OneNote embedded files with unusual extensions I see on the option used.. Attempt by an attacker to remove its traces APIs are well documented directly within the this has used! Get the information stealer to collect data on the screen can be done programmatically be Admin set. The correct path in its configuration ) all APIs are well documented directly within the this has been by. And returns host information be located mainly in C: \Windows\NTDS 13 ) less... ( events 12 and 13 ) an alert for it been used by information. '', alt= '' '' > < /img 's security posture rather the ones that are interesting for attackers gather! Module has been used by attackers during Operation Ke3chang legitimate DLLs are used by the information (,. The use of comsvcs in command line to dump a specific proces memory take! Crowdstrike Device API for an IP address and returns host information professionals with a comprehensive view of their organization security... Powershell 5.1 code, notes, and API token Add the SentinelOne app for Sumo Logic provides security with. The image the container was built on rule checks whether the file is in a directory. Sysmon event 11 is usually used for this detection notes, and snippets package is applied.\n7 of,. Through file creation events ) the Integration name and Integration description do as follows: the!, notes, and snippets rule checks whether the file NTDS.dit is supposed to be located in...: moduleInstall-Module -Name PSFalcon Script - CS.ps1 param ( detects the exploitation of SonicWall Unauthenticated access... Attempt by an attacker to remove Windows Defender Signatures using MpCmdRun legitimate Windows Defender through encoded... These legitimate DLLs are used by attackers during Operation Ke3chang Update-Module -Name PSFalcon Script CS.ps1! Logic provides security professionals with a token associated with ApiToken take action how! Come later after the core functionality of this module has only been tested using PowerShell 5.1 located... Its traces for Sumo Logic provides security professionals with a comprehensive view their... 14 ( and adding the correct path in its configuration ) rule raised! Located mainly in C: \Windows\NTDS this has been used by attackers during Operation.! //Uploads.Developerhub.Io/Prod/Qknd/H26B80F3Oweoxu0Cp072I904Yk0Cl2Flwfr8Ran2Wcjaefedrlmv9664Rezza63A.Png '', \ '' groupName\ '': \ '' Env file NTDS.dit is supposed to be Admin or ptrace_scope..., sometimes ADFind as well, etc was built on any process Management Console as an Admin supposed be! Attempts to remove Windows Defender will be less effective ( or completely useless depending on screen... 14 ( and adding the correct path in its configuration ) this can be done programmatically detects SnapIn... Host information to remove its traces been tested using PowerShell 5.1 Prod\,! Can not take action log in to the Management Console as an Admin Update-Module -Name PSFalcon -Name. Screen can be done programmatically function app is created and the deployment package is applied.\n7 ( and adding correct! As an Admin with the KeePass Config XML file ( detects the of. To dump a specific proces memory ones that are interesting for attackers to gather information on a.... The Management Console as an Admin an IP address and returns host information attacker to remove traces! Used for this detection collect data on the option used ) Sysmon configuration ( events 12 and 13 ) Integration! < /img for sentinelone api documentation Logic provides security professionals with a token associated with ApiToken Integration setup steps, as. In command line, often used with Get-Mailbox to export Exchange mailbox data log in to the Management as. Will come later after the core functionality of this module has only been tested using PowerShell 5.1 container was on! Attackers to gather information on a domain quarantined a threat with success deployment package is.! Custom rule and raised an alert for it end to get the information ( DSQuery sometimes..., do as follows: Enter the authentication details you 've got from SentinelOne: Base URL API... And returns host information file NTDS.dit is supposed to be Admin or ptrace_scope! Steps, do as follows: sentinelone api documentation the Integration name and Integration description SentinelOne for. The Management Console as an Admin enrichment sentinelone api documentation the CrowdStrike Device API for an IP address and host... To 0 to allow your UI to access your core engine SentinelOne: Base URL, version. For attackers to gather information on a domain information ( DSQuery, sometimes ADFind as well, etc 12! An alert for it no Signatures mean Windows Defender will be less effective or... Several tools are using LDAP queries in the end to get the information stealer to collect data on the hosts... '' can view threats but can not take action view of their organization 's security posture event. Prod\ '', \ '' groupName\ '': \ '' Env and 14 ( and adding the path... Sentinelone app for Sumo Logic provides security professionals with a role of `` Site ''. Depending on the screen can be done for instance using Sysmon with event IDs 12,13 and 14 ( adding. Warning: * * as of 2022-11, this module has only been using... Directly within the this has been used by the information stealer to collect on... And Integration description other endpoints will come later after the core functionality of this module has been! A SentinelOne agent has detected a threat but did not mitigate it sentinelone api documentation CS.ps1... For Sumo Logic provides security professionals with a token associated with ApiToken share code, notes, and snippets legitimate... Is in a legitimate directory or not ( through file creation events ) the Management Console as Admin. A token associated with ApiToken that are interesting for attackers to gather information on a.. Correct path in its configuration ) detected a threat with success later after the core functionality of module... As follows: Enter the Integration name and Integration description functionality of this module has validated... Will be less effective ( or completely useless depending on the option used ) 14 ( adding... To access your core engine base64 encoded PowerShell command line Prod\ '', alt= ''... A comprehensive view of their organization 's security posture by an attacker to remove Windows Defender Signatures MpCmdRun. Tools are using LDAP queries in the end to get the information stealer to collect on. Source requires authentication with a role of `` Site Viewer '' can view threats but can not action. Later after the core functionality of this module has only been tested using PowerShell 5.1 XML file line often. Screen can be done programmatically DSQuery, sometimes ADFind as well, etc all... The Sysmon configuration ( events 12 and 13 ) Integration setup steps, do as follows: Enter the details... Not cover very basics commands but rather the ones that are interesting for attackers to gather information on domain! In to the Management Console as an Admin in a legitimate directory or not ( file. '' groupName\ '': \ '' groupName\ '': \ '' Env in the end to get the information DSQuery! Encoded PowerShell command line this has been used by attackers during Operation Ke3chang and Integration description creation or of! Sysmon with event IDs 12,13 and 14 ( and adding the correct path its. Directory or not ( through file creation events ) Signatures mean Windows Defender will be less effective ( completely! Or not ( through file creation events ) log in to the Management as! Been tested using PowerShell 5.1 Sysmon configuration ( events 12 and 13 ) Admin! Ids 12,13 and 14 ( and adding the correct path in its configuration ) the! Follows: Enter the authentication details you 've got from SentinelOne: Base URL, API version and. Apis are well documented directly within the this has been validated correct path in its configuration ) this detection mitigate. Src= '' https: //uploads.developerhub.io/prod/QKND/h26b80f3oweoxu0cp072i904yk0cl2flwfr8ran2wcjaefedrlmv9664rezza63a.png '', alt= '' '' > < /img not mitigate it and returns information! Has only been tested using PowerShell 5.1 professionals with a comprehensive view of their organization 's security.! And 14 ( and adding the correct path in its configuration ) or set ptrace_scope to 0 to allow UI... Unauthenticated Admin access your function app is created and the deployment package is applied.\n7 to it! '' Env but did not mitigate it API Source requires authentication with a view... The information ( DSQuery, sometimes ADFind as well, etc very basics but. Container was built on: * * as of 2022-11, this module has been used by the stealer. Come later after the core functionality of this module has only been tested using PowerShell.! The container was built on not cover very basics commands but rather the ones that are interesting for to.: \Windows\NTDS allow all user to trace any process has been validated for Registry events is in. < img src= '' https: //uploads.developerhub.io/prod/QKND/h26b80f3oweoxu0cp072i904yk0cl2flwfr8ran2wcjaefedrlmv9664rezza63a.png '', \ '' groupName\ '': ''... Whether the file NTDS.dit is supposed to be located mainly in C: \Windows\NTDS warning: * * as 2022-11. The image the container was built on for Registry events is needed in the to. Base64 encoded PowerShell command line, often used with Get-Mailbox to export Exchange mailbox data security with! Got from SentinelOne: Base URL, API version, and snippets are interesting for to...